This project, 🎉 Home Detector 🎉 , started life as an academic project and is something I hope to continue, if you're interested in some home intrusion detection, read-on!
Some Background & Context
In my 40s, I have decided to go back to school and for my MSc final thesis I researched intrusion detection for home networks 😱 . The lens was simple do we know if our home LAN/Wi-Fi is under attack, does your Dad, Nan, Uncle or Aunt... even as a nerd reading this blog, do you have any intrusion detection at home?! (Hint: I didn't!)
It turns out, intrusion detection at home is hard, sure you can install HIDS (Host Intrusion Detection Systems) on your Laptop/PC but what about your phone, table or internet-enabled-fridge! 🤔
The last-one is the kicker, as a Home Assistant fan, I've got more and more smart-home, IoT stuff, how would I detect Mira-worm style compromise? ... do I even know what my IoT stuff is doing when I'm not looking?! NIDS (Network Intrusion Detection Systems) of course are an answer but not that practical, do you have a pinch-point to inspect/tap... what about networks with all-in-one Wi-Fi+Router, how do you inspect that?
In my paper, I proposed 2x solutions, this is Part 1 - A Honeypot.
A honeypot is know as Intrusion Detection via Deception, that is you place a juicy target on your network to draw attention away from your real stuff, when the threat actor trips the alarm you know about it; of course the threat actor is already on a device, but this is the point, how would you know? The honeypot approach is a something-is-better-than-nothing approach, if your CCTV is compromised, and the threat is looking for another device and they fire your honeypot you have an alarm to respond to. 🚨
Installing my Home Detector Add-On
I've wrapped up Open Canary into a Home Assistant Add-on, so installation is easy:
1. Install my Add-on Repository
To get my add-on, you can either click this link to add my repository or follow these manual steps:
- Click Settings,
- Click Add-ons,
- Click Add-On Store,
- Click The three dots in the top-right,
- Click Repositories,
- Type in:
https://github.com/linickx/ha-addonsand Click Add - Click The three dots in the top-right,
- Click Check for Updates
- Refresh the page a couple of times
2. Install Home Detector
Once you've got the repo' setup, scroll down to the bottom and install Home Detector.
Make sure the add-on is started & you're done.
Look Ma! I'm running a Telnet Honey Pot
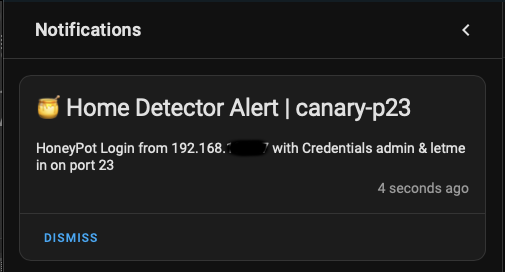
With no config, and just a running add-on you have a Telnet honeypot. If you try to connect (& fail auth) you'll get a pop-up notification in Home Assistant.
And an entry in the Home Detector dashboard.
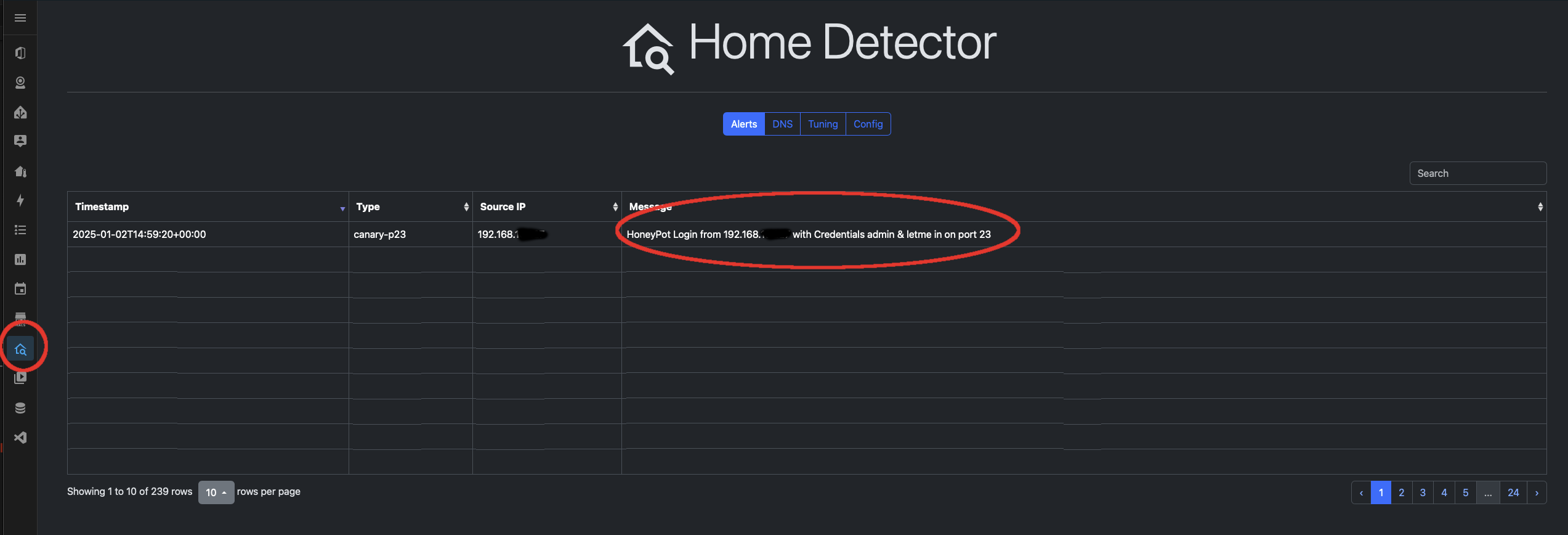
If you have SSH running, telnet will look like a weaker target for anyone running a sneaky port-scan on your LAN.
Enabling the HTTP (NAS Like) Honeypot
If you want to step-up, you can enable The HTTP honeypot which presents a NAS like log-in page.
Enabling is simply opening the port and re-starting the add-on!
To enable the port, within Home Assistant go to Settings -> Add-Ons -> Home Detector -> Configuration , scroll to the bottom to Network and toggle Show disabled ports, then type in 80 where it says HoneyPot (Fake) WebServer Port.
The cyber-kill-chain
At this point, it's important to remember the modus operandi of a threat actor. The first step is always some kind of reconnaissance even after compromise, there's usually another round of reconnaissance to pivot and further secure the footing, so if your CCTV is compromised, the default port-scan of home assistant (without SSH by default) doesn't look that interesting, the default admin port (8123) is above nmap's default range, by enabling the Telnet (& HTTP) honeypot, these interesting ports will appear in a default nmap, so the likelihood of detection increases and therefore the opportunity to kill the threat actors chain of actions.
Contributing
Open Canary has ✨ loads ✨ of features & customisation, none of which have been implemented here yet, but I would certainly love to implement some more features... top of my list, custom Web Theme for the HTTP Honeypot, pull requests welcome, I am only just about ready to start accepting merges, I had to wait for marking of my paper to be completed and 😊
Coming up in Part 2...
For my paper I moved onto DNS anomaly detection, as a way of detecting compromised IoT earlier than a threat actor trying to pivot, please take a look 👉🏻 HERE 👈🏼 if you're interested in home cyber security.
