After implementing an Open-Canary based home honeypot in part 1, for my research project I moved onto implementing a DNS based anomaly detection intrusion detection system ... try saying that 3 times fast after a few pints! 😆
📝 This post assumes that you already have Home Detector installed on your Home Assistant server.
The idea is an internal, home network honeypot would only trigger if there was already a threat on your LAN, in order to attempt to catch someone/something earlier I built a simple DNS anomaly detection engine; there's an important gotcha here, although the honeypot was low-effort-drop-in (plug-n-play), DNS inspection is a bit more technical you will need a method of updating the DNS settings on your IoTs to make this work, either by changing your DHCP setting, doing something on your router, or by touching each device (if they support custom DNS that is!).
How it works
Home Detector acts as a local DNS forwarder, point your IoT/Smart-Things at it and for 30days it'll start recording the DNS lookups. After 30days, it'll consider what it saw as the baseline and therefore anything new after that point will generate an alert.
The baseline is per IOT thing, which can be a single host IP, a range of IPs or a subnet depending on your home setup, so you're going to need the real-source-ip of your IOT thing hitting Home Assistant (The Home Detector Add-on)
Enable DNS Interception
The DNS interception is opt-in which means there's 2x steps:
Step 1
The first is point your system at it, i.e. update the DNS settings of the IOT device to have Home Assistant's IP as a DNS server.
How you do this will vary, you might be able to update your router to use Home Assistant as the DNS server for all your LAN. You might be able to change the DNS server on the IoT device it's self. Or if you cannot change DNS anywhere, disable DHCP on your router and install a DHCP server add-on and set the DNS server IP to that of Home Assistant.
Step 2
It's ok if all your DNS hits Home Detector (Home Assistant) as by default, the add-on will pass through, not touching the responses and everything should continue to work.
To enable the detection, under add-on settings, enable interception for specific IP addresses, like this:
Tweak any other settings you fancy from the Docs as necessary.
Enjoy the DNS goodness
Within the Home Detector Dashboard, there are 3x views.
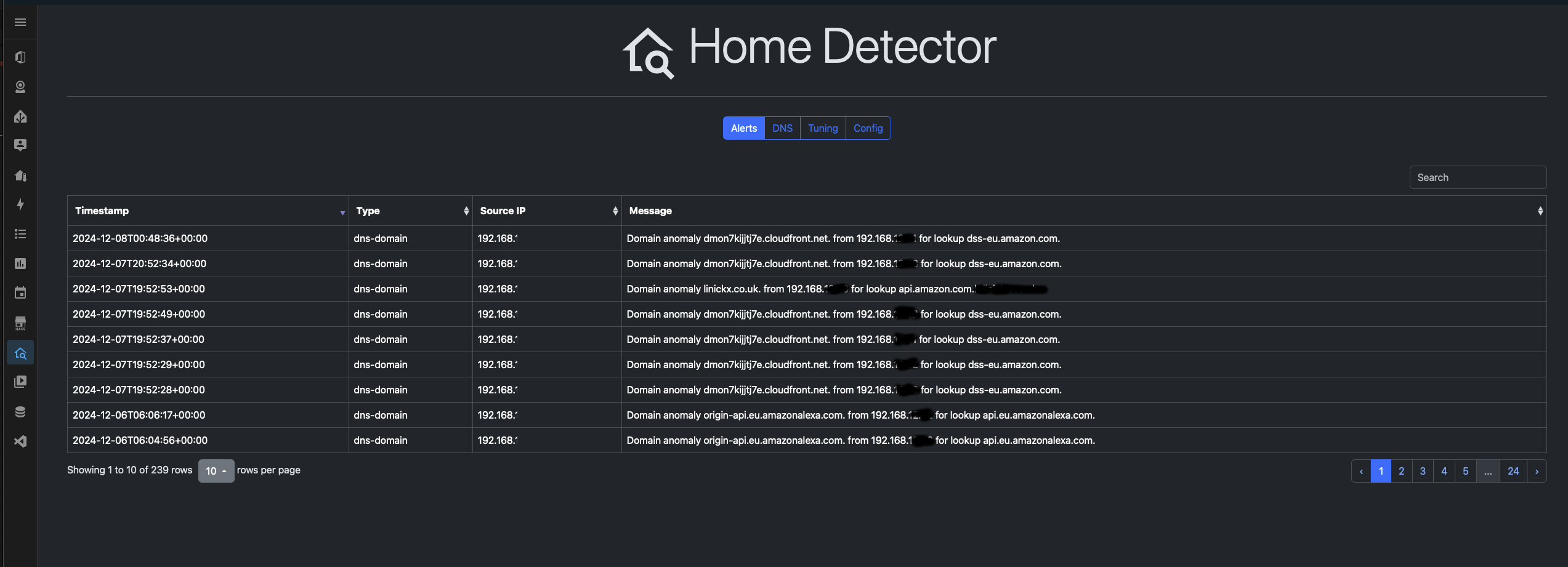
(i) The Alerts
By default, Home Detector will generate dns-domain alerts, there are alarms for new domains being queried, the SOA record is used to determine domain ownership.
If you enabled Detected on Host Query then Home Detector will generate dns-query alerts, these are alarms for new host queries.
Here you can see a bunch of Amazon Alexa alerts on my console, these are new domains that the very talkative little box has started calling out to...
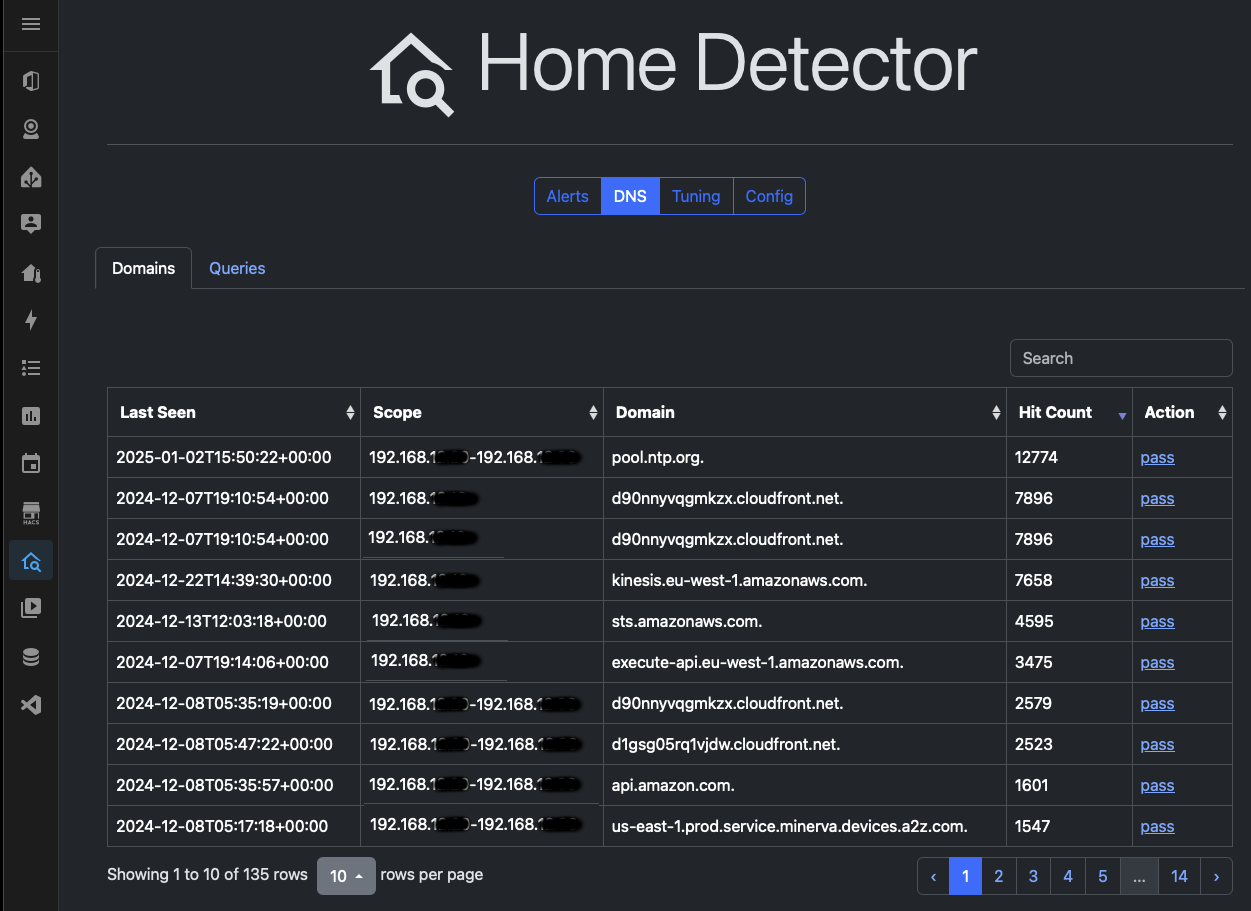
(ii) The DNS Domains
On the Domains page, you can review the domains that are in pass state or block state, for the first 30days (by default) all domains will be in pass, only after the baseline is created will blocks start to appear.
🔥 By Default, Block does not mean Block, it means 🚨 alarm 🚨 (perhaps not my best choice). Only if you enable the DNS Firewall under settings will the DNS be blocked, Home Detector will send
NXDOMAIN(domain not found) responses.
This is what my domains page looks like, the first range for ntp.org is for my shelly devices, the next 5x are for my heating/themostat, and then the bottom ranges are for alexa's... as you can see there's 135 row, quite a lot of learnt traffic in my LAN.... and this is JUST the IoT devices, Phones/Laptops/etcs do not log here and in my documentation I warn against doing that 😬
(iii) The Queries
Like the domains page, the queries page allows you to review all the look-ups from a device in either pass or block state.
Why am I doing this?
If you've got this far, 👍🏼 nice 👍🏼 !
The point of this is to monitor what your IoT/Smart-Things are doing, you should get an idea quickly of what is normal, and IF a device got compromised it would certainly start doing different queries, like downloading malware-firmware, or downloading scripts from compromised sites... Command-and-Control needs DNS to function.
A word of Warning
The noise from my home stuff has been low, shelly, etc have a couple of domains and everything works as expected, but with 👾 Amazon Alexa devices there be monsters ahead! 👾 ... those things seem to be constantly using new hosts and new domains, it's eye-opening but also annoying, so intercept those things with care.
Next Steps
There's a fair amount of future work I'd like to look at, changing domains from pass to block by typing instead of drop-downs is quite annoying 💩 ... also, I'd like to implement some built-in signatures to assert what is normal before the learning phase is completed. Pull requests are welcome but the first thing I need to do is update all the dependencies, as since finishing the project, github's dependabot has been going mental!
